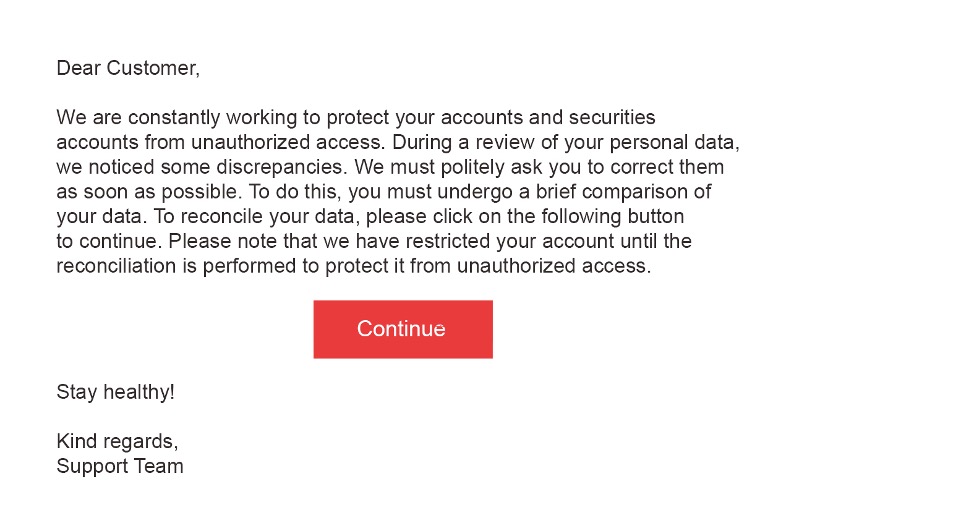
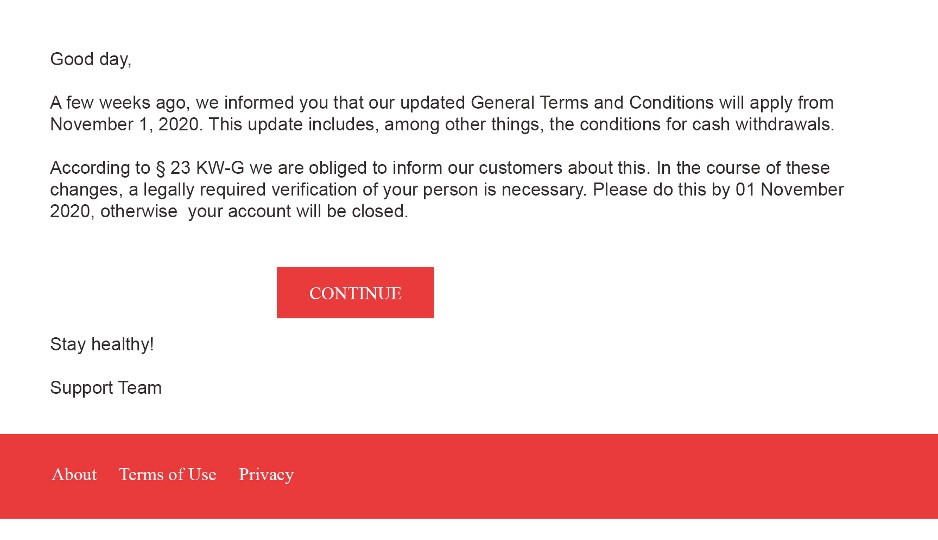
Fake or real – Can you spot the difference?
Data is the new currency in the digital age. Whether it’s a username, password, or bank details, all of this information is highly valued these days. Companies use information about browsing behavior to display targeted advertising and thus influence and control purchasing decisions.
But data and information are not only valuable to companies for marketing purposes, they can also be used profitably by unauthorized third parties.
What strikes you about the following message?
Consider the message above! Do you notice something? Think of a nice reminder from your savings bank?
And what do you think about reading this nice email? Would you click “Continue” with a clear conscience?
If so, you would now have a huge problem in practice. This is “phishing”. The cybercriminal “fishes” (phishing: artificial word from the English word “fishing”) for information on the Internet.
Basically, this is understood to be the attempt to impersonate a reputable communication partner via fake messages, e-mails, or websites and thus elicit trustworthy information from its victim or induce them to engage in other harmful activities. It is particularly dangerous that phishing e-mails and the associated websites are often very elaborately designed and can thus authentically imitate the original designs. The corporate design, logo, color scheme, and font also look realistic and make the user believe that they are communicating with the “real” savings bank, for example. Of course, cybercriminals particularly like to use institutions that users normally trust. This makes “phishing” particularly insidious for older people. Users should therefore be particularly suspicious of messages from large banking groups and, if in doubt, never click on links or similar provided there. Links to phishing websites can also appear in postings on social networks. Here, a well-known brand is often used as a priority.
What can happen to you and your employees?
For example, phishing can lead to data theft for you as an individual or even illegal account debits. It becomes even more dangerous when attacks are made on your company’s critical infrastructure. In the past, attacks on European and US utilities – including nuclear power plant operators – could even be observed here. In the worst-case scenario, this could involve scenarios you’d rather not imagine. Many cases also involve financial fraud, skimming of trade secrets, or military information. If you or your employees are affected by phishing yourself, the worst-case scenario is not exclusively financial damage. The loss of confidence in your company can also be seen as damage. Many of those affected even blame themselves and believe that their own ignorance has led to this damage. Nevertheless, it is helpful if you and your employees adopt strategies to avoid being part of a very large group of victims in the first place.
The phishing attack in 3 steps
To best protect yourself from attacks, you should know the three components of the phishing attack.
In the first step, you are contacted via an electronic means of communication such as e-mail, text message, or telephone. The attacker always pretends to be a trustworthy person or company (e.g., a bank). Finally, the attacker asks you to disclose confidential personal information (e.g. login credentials or credit card numbers) or to click on links.
What can you look out for?
From now on, check every email, especially from your banks and credit institutions. If all three components of the phishing attack are met, then you should become suspicious. If you are unsure, then when in doubt, call your personal advisor or ask your company’s IT department or CISO directly. The guiding principle is that reputable companies like banks would never force you to divulge confidential data via email. Nor will a bank ever decide from one day to the next that your credit card is invalid or that your bank account has been spontaneously blocked. In this case, you have to ask in any case. If you take a look at the sample texts shown here, you will be able to understand roughly which scams classic fraudsters use and how you can unmask them and thus render them harmless.
Also, you can hover over a link without clicking on it directly. Hovering the mouse over the link displays the link target without opening it.
What are the known types of phishing?
- Email phishing is the most widespread and was therefore also used in our examples. Be especially vigilant here.
- Website phishing is when attackers use copies of trusted websites to trick you as a potential customer. It often involves an input screen where you are asked to enter your original user data. The scammer can reuse them on the original website. Pop-ups also belong to website phishing and are a popular way to get your data.
- “Vishing” refers to the tapping of information over the telephone (voice phishing). Here, the attackers try to persuade you to disclose confidential information over the phone. Be especially alert to automated calls.
- The same principle via SMS is called “smishing”. Here, too, attackers can ask you to disclose information, call up links, or download apps.
- Social media phishing works in the same way as e-mail phishing described above. Here, attackers try to obtain your confidential information via social media channels (e.g. Facebook, Instagram, TikTok).
What should you do now?
Phishing has many faces. You and your employees can encounter it at any time in the digital world. Now you know the most common types of phishing and have a first impression of the frequently occurring scams. This increases the likelihood that you won’t choose the click that brings them nothing but trouble at the crucial moment.
We are also happy to support your company with our Cybersecurity Awareness training, in which we highlight risks and use simple tips to teach your employees what they can and must do themselves to ensure the protection of your company in the digital world.
We offer you the whole range of security instruments from code reviews of your software products, quick checks of your organization, awareness training of your employees, to penetration testing of your servers and IT landscape and support you in the implementation of your individual holistic cybersecurity plan.
Together we can master the future!